| Symantec Mail Security 8160 |
OVERALL RATING | |||||||||||||||
|
||||||||||||||||
|
||||||||||||||||
|
||||||||||||||||
|
||||||||||||||||
By Joel Snyder
Network World, 04/11/05
Original Artcle on Network World Web Site
Symantec's new Mail Security 8100 Series appliance offers a twist on spam management. It limits the amount of network bandwidth spam can consume. In our exclusive Clear Choice test of the Mail Security 8160, we found that when the bits start flying it manages the load on corporate mail servers quite well, providing a good first line of defense in reducing the amount of spam that enters the network.
Placed in-line between corporate mail servers and the Internet, the Mail Security 8160 appliance (Symantec picked up the technology last year when it bought TurnTide) categorizes e-mail traffic flowing through it into one of 10 buckets based on the spam history of the originating IP address. It then manages the amount of bandwidth each bucket can consume.
The Mail Security 8160 determines an IP address' spam history in two ways. It's connected to Symantec's Brightmail on-line service - a requirement to using this product - which provides a global view of IP addresses that have been sending spam. Second, the Mail Security 8160 contains the Brightmail engine and analyzes e-mail traffic to determine the spam content for each IP address. Every IP address falls into a bucket based on a percentage: How much of the mail received from this IP address is spam?
Although you can control the throttling parameters within each bucket, Symantec ships the Mail Security 8160 with a set of example values that represent a staged approach to implementation. The bandwidth controls set against the offending IP addresses get more aggressive as you move from Stage One to Stage Five. Note that the 8160 only shapes mail traffic on the SMTP port (Port 25). It doesn't control any other traffic or mail on other ports.
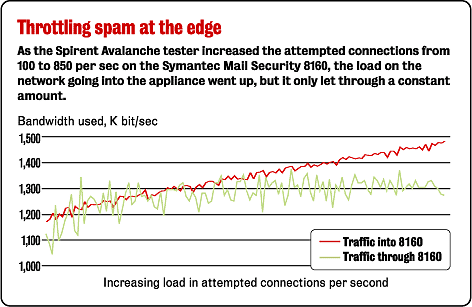
The Mail Security 8160 is designed to handle a huge volume of e-mail, and it lives up to those claims. Symantec claims a capacity of about 550 messages per second, but our testing showed it topping out at 850 messages per second. That's a massive number of messages, almost 75 million a day. If you were going to send that much mail through this product, you'd want a high-availability solution, and the Mail Security 8160 is designed to operate as an active/passive two-node cluster with automatic failover and database synchronization.
Although the Mail Security 8160 can operate as either a routing or bridging device, we installed it as a transparent bridge directly in front of our test mail server. We recommend that configuration because you don't want to send anything but e-mail through this device because it has virtually no management, control or monitoring capabilities. The Mail Security 8160 also is missing an out-of-band management port.
The lack of management and monitoring is disconcerting. Although the Mail Security 8160 ships with a Web-based GUI, there's very little information inside it about how mail is being throttled.
The 8160 has a series of built-in graphs that give broad summary information about bandwidth utilization and how much mail is flowing through the system, but these are coarse reports with long timeframes. They'll be excellent for showing upper management how well the Mail Security 8160 is cutting the load of spam, but not so good for diagnosing problems. Although we worked with the 8160 for a week, we didn't get a single message in the event log. From the monitoring tools in the GUI, we had no idea if it was successfully updating Brightmail data or even if the system was being overloaded - although we knew that it was based on a console command to show CPU utilization. There is no support for SNMP monitoring of the system.
While the management GUI is easy enough to figure out, there's not a lot of options to configure. The essence of the product all fits on a single screen: the list of buckets and how bandwidth is managed in each of them.
So how well does it work?
|
|
|||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||
Answer: It's not perfect but pretty close. We sent large volumes of mail through the Mail Security 8160 at a rate of 850 messages per second. We divided our senders into three categories: 0%, 50% and 100% spammers (see how we did it ). The 100% spammers were heavily throttled, as we had planned, getting just a few messages per hour through to the mail server. Although the 0% spammers were not throttled, the Mail Security 8160 was stressed by the load and did drop a few messages that it shouldn't have. When we tested to establish a base performance level without any spam and without any added real-world latency, the Mail Security 8160 didn't drop any messages it shouldn't have. With the 50% spammers, the box throttled the traffic, but not exactly in coordination with the policy we had selected.
We tried having the 50% spam sender bucket throttled to only a few kilobits per second (192K, then 128K and finally 64K) and didn't see the Mail Security 8160 honor that configuration very well. For example, we saw virtually no change in behavior between the 64K and 192K throttles. However, our feeling is that hitting these bandwidth limits right on the money isn't very important when it comes to throttling incoming spam, and most network managers will be happy with the results - even if they are very difficult to explain.
It's important to view the Mail Security 8160 as one piece in a much bigger anti-spam plan of attack. It does not identify and block spam: It throttles back IP addresses that send spam. The more they send, the more they get throttled. The idea is to take some of the load off of a content-based anti-spam solution by peeling off the most obvious offenders. If you're only getting a million messages a day, you don't need something like this -traditional anti-spam products (such as Symantec's Brightmail) do a great job. But if you're seeing a million messages an hour, the Mail Security 8160 can help a great deal by easing the load on the rest of the network.